| Security Operations Center (SOC) Analyst |
|---|
| A Security Operations Center Analyst monitors an organization’s digital systems to identify, investigate, and respond to security threats. They review security alerts, analyze suspicious activity, support incident response, and document actions taken to protect systems and data. |
Cyber threats are increasing every day, and organizations of all sizes face risks to their systems and data. Even small security issues, such as unauthorized access or system disruptions, can affect operations and trust if they are not handled early.
To manage these risks, organizations need a structured way to continuously watch their digital environments and respond when something goes wrong. This is where centralized security operations play an important role by helping teams stay aware of security activity and take timely action.
At the center of these operations is the Security Operations Center Analyst, commonly known as a SOC Analyst, who reviews security alerts, investigates unusual behavior, and supports actions that protect systems and data.
This blog explains the SOC analyst roles and responsibilities in a simple and beginner-friendly way, helping readers understand how the role fits into modern security operations.
What is Security Operations Center (SOC)?
A Security Operations Center (SOC) is a team that watches over an organization’s digital systems to keep them safe. It helps detect security problems early and respond quickly when something goes wrong. In simple terms, a SOC ensures that computers, networks, and data are continuously monitored and protected.
Who is a Security Operations Center Analyst?
A SOC Analyst is a cybersecurity professional who works in a Security Operations Center. Their primary role is to monitor an organization’s digital systems and identify potential security issues before they cause harm—activities that form the core of a typical SOC analyst for job description.
They focus on reviewing security alerts, observing system activity, and supporting the response to suspicious behavior. By continuously watching over networks, applications, and devices, they help ensure that digital environments remain secure and stable.
SOC Analysts act as the human layer in security operations. While security tools generate alerts and data, the analyst reviews this information, understands what it means, and helps decide the next steps when an issue is detected.
In simple terms, a SOC Analyst helps organizations stay aware of security risks and respond to them in a structured and controlled way. To perform these tasks effectively, analysts rely on various SOC analyst tools to monitor activity, generate alerts, and support investigations.
Roles and Responsibilities of a SOC Analyst
The SOC analyst responsibilities focus on how security alerts are reviewed, incidents are handled, and issues are resolved in a structured way. These responsibilities ensure that security events are managed consistently, from initial detection to final resolution, without affecting normal operations.
| Responsibility Area | What It Involves | Why It Matters |
|---|---|---|
| Security Monitoring | Observing system, network, and user activity to maintain continuous visibility across the environment | Enables early detection of unusual behavior before it escalates into serious incidents |
| Alert Triage & Prioritization | Reviewing and categorizing alerts based on risk, relevance, and urgency | Ensures critical threats receive immediate attention while reducing alert fatigue |
| Suspicious Activity Investigation | Analyzing patterns, logs, and timelines to determine whether activity represents a real security threat | Prevents false assumptions and supports accurate, evidence-based decisions |
| Incident Response Support | Coordinating containment actions and escalating confirmed incidents appropriately | Limits the spread of threats and reduces operational and business impact |
| Documentation & Evidence Handling | Recording actions, timelines, and findings during security events | Supports accountability, audits, and future security improvements |
| Continuous Improvement | Reviewing past incidents to strengthen detection methods and response processes | Helps security operations evolve and remain effective over time |
1. Monitor Security Activity and Maintain Visibility
Monitoring security activity means keeping a close watch on what is happening across an organization’s digital systems using monitoring tools such as SIEM platforms (like Splunk, QRadar, or Microsoft Sentinel). This includes observing system activity, network traffic, applications, and user actions to ensure everything is operating as expected.
Maintaining visibility allows security teams to clearly see and understand this activity. When systems are continuously monitored through centralized security dashboards and endpoint tools (EDR/XDR), unusual behavior can be noticed early, before it causes serious impact.
This focus on early visibility reflects widely accepted security practices that rely on continuous monitoring to detect threats early and respond to incidents effectively.
On a daily basis, monitoring helps teams stay aware of both normal and unusual activities. This may include noticing system usage at unexpected times, changes in application behavior, or unfamiliar connections within the network. These signs do not always indicate a security incident, but they help build awareness of what is happening across the environment.
By regularly reviewing activity and acknowledging events as they occur, security teams reduce gaps in awareness and strengthen their ability to respond in a timely and structured manner.
2. Prioritize Alert Quality
Alerts are notifications generated when SOC analyst tools such as SIEM platforms like Splunk, QRadar, or Microsoft Sentinel notice something unusual. Prioritizing alert quality means deciding which alerts are important and which are at low risk.
Some alerts point to real security issues, such as unexpected logins, unusual system behavior, or unfamiliar network connections, while others are triggered by normal system activity. This responsibility involves reviewing alerts carefully and focusing attention on those that may cause harm if ignored using alert dashboards and case management systems.
By prioritizing alerts, security teams ensure that high-priority alerts are handled first, and less important alerts do not distract attention. This prevents critical warnings from being missed and keeps responses focused and timely often supported by SOAR and ticketing tools.
This pattern of awareness improves accuracy and reduces unnecessary escalation. Such disciplined triage aligns with widely accepted SOC practices that emphasize focused investigation and signal quality as essential to effective security operations.
3. Investigate Suspicious Activity and Determine Impact
Investigating suspicious activity means looking closely at alerts or behavior that cannot be ignored to understand what is really happening using investigation tools such as SIEM search, log analysis platforms, and endpoint detection tools (EDR/XDR). This role focuses on confirming whether an activity is normal or a real security issue.
Suspicious activity often appears when multiple unusual actions occur together, rather than as a single event. For example, repeated failed login attempts, access from unfamiliar locations, unexpected system changes, or unusual connections to external systems may indicate a potential problem when correlated across logs, endpoints, and network monitoring tools. These signs help analysts decide whether further action is needed.
The goal of the investigation is to determine the impact. This includes understanding whether systems were accessed without permission; data may be exposed, or normal operations could be disrupted if the issue continues.
By investigating carefully, security teams avoid unnecessary disruption while ensuring that genuine threats are identified and addressed. In simple terms, this responsibility helps confirm what happened, how serious it is, and what needs to be done next.
4. Support Incident Response and Containment
Supporting incident response and containment means taking action once a security issue is confirmed. The focus shifts from understanding the problem to stopping it from spreading and causing more damage.
This responsibility involves helping control the situation in a calm and organized way. Actions are based on confirmed information, not assumptions, so that systems are protected without disrupting normal work unnecessarily with the help of incident response platforms and automation tools (SOAR).
In simple terms, containment may include isolating affected systems, block suspicious connections using firewalls or intrusion prevention systems (IPS), or restricting compromised accounts. These steps help limit the impact of the incident while further investigation or recovery continues.
Clear communication is an important part of this role. Confirmed incidents are shared with the right teams so that response actions can begin quickly and without confusion.
By supporting incident response and containment, security teams help reduce damage, maintain stability, and restore normal operations safely.
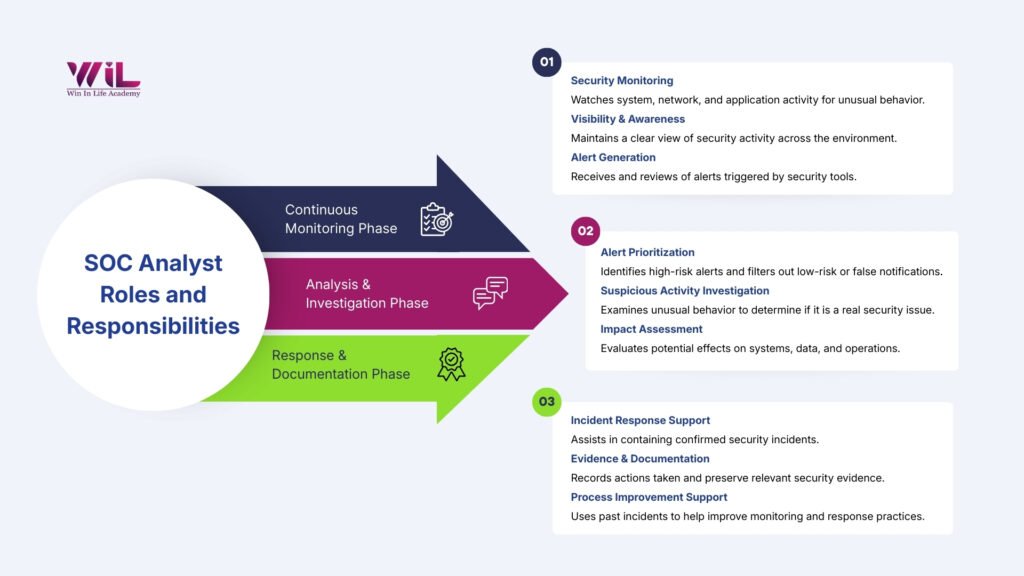
5. Record Actions and Preserve Evidence
Recording actions means writing down what was done during a security incident, step by step. Preserving evidence means saving important information safely so it can be reviewed later if needed.
This responsibility is important because security events can move quickly. Without clear records, it becomes difficult to understand what happened or explain how the issue was handled.
In simple terms, this role involves noting key details such as what alert was seen, what was investigated, what actions were taken, and when each step occurred. Information like system logs or activity reports is saved carefully, so it remains accurate and unchanged.
Keeping proper records helps teams review incidents with confidence, answer questions during audits or reviews, and avoid relying on memory alone.
Over time, these records also help improve security operations. By looking back at past incidents, teams can learn what worked well, identify gaps, and strengthen how future issues are handled.
Cyber Security Course
Build practical, industry-aligned skills to work across real-world security operations environments. Learn how cyber threats are identified, monitored, investigated, and responded to, with a strong focus on system protection, ethical practices, and operational security used in modern organizations.

Duration: 6 months
Learn at your own pace
Skills you’ll build:
Threat Monitoring & Incident Response Basics
Network & System Security Essentials
Ethical Hacking & Vulnerability Awareness
Log Analysis & Security Event Investigation
Security Best Practices, Risk Awareness & Compliance
Other Courses
- Advanced Diploma in AI and ML
- Data Science & MLOps Professional Certificate
- Advanced Diploma in Digital Marketing + AI Essentials Course
Skills Required to Become a SOC Analyst
To work effectively in security operations, individuals need a mix of technical understanding, analytical ability, and clear communication. These skills are practical and can be developed over time and form the foundation of a typical SOC analyst career path.
Key skills include:
- Basic technical knowledge of operating systems, networks, and applications
- Understanding of security alerts and system activity
- Analytical thinking to review information and identify patterns
- Attention to detail to notice unusual or unexpected behavior
- Problem-solving ability to assess situations and support decisions
- Clear communication skills to share findings with other teams
- Willingness to learn and adapt as systems and threats change
Conclusion
Effective security operations depend on clear processes, consistent actions, and informed decisions. When these elements work together, organizations can handle security issues calmly and without unnecessary delay.
The responsibilities discussed in this blog show how security work moves from monitoring and investigation to response and documentation in a structured way. This approach helps ensure that issues are addressed carefully, evidence is recorded properly, and lessons from past incidents are used to improve future readiness.
Win In Life Academy’s Cyber Security Course with Online Certifications helps learners understand security operations in a simple and practical way, preparing them to work confidently in SOC environments as a Security Operations Center Analyst.
By understanding how these responsibilities connect, readers gain a clear view of how security operations function in real-world environments. Strong operational foundations help organizations stay stable, protect trust, and respond confidently as security challenges continue to evolve.
Frequently Asked Questions (FAQs)
1. Why is the Security Operations Center Analyst role important in today’s organizations?
SOC Analysts play a vital role in keeping organizations secure and operational. As digital systems become more complex, continuous monitoring and structured response are essential. SOC Analysts ensure that security risks are identified early and handled correctly, helping organizations maintain trust, stability, and uninterrupted operations.
2. Is the SOC Analyst role suitable for beginners in cybersecurity?
Yes. The SOC Analyst role is often considered one of the best entry points into cybersecurity. It focuses on understanding how security operations work in real environments, making it ideal for learners who want to build strong fundamentals before moving into advanced security roles.
3. What kind of learning mindset is important for a SOC Analyst?
A SOC Analyst benefits from curiosity, patience, and a willingness to learn continuously. Security environments evolve constantly, and analysts who enjoy understanding systems, investigating issues, and improving processes tend to succeed and grow confidently in this role.
4. Do SOC Analysts work independently or as part of a team?
SOC Analysts work as part of a coordinated security team. Collaboration is a key aspect of the role, as analysts regularly share findings, escalate issues, and support response efforts together. This teamwork helps ensure accuracy and consistency during security operations.
5. How does SOC experience help long-term career growth?
Working in a SOC provides exposure to real-world security scenarios, tools, and processes. This experience builds a strong operational foundation that supports growth into roles such as incident response, threat analysis, security engineering, or governance-focused positions over time.
6. Is technical expertise more important than analytical thinking in SOC roles?
Both are important, but analytical thinking plays a critical role. Tools generate information, but SOC Analysts must interpret that information correctly. The ability to connect details, assess context, and make informed decisions is essential for effective security operations.
7. How do SOC Analysts contribute beyond handling incidents?
Beyond responding to incidents, SOC Analysts help improve security by identifying patterns, documenting lessons learned, and supporting process improvements. Their insights help organizations strengthen detection methods and respond more effectively to future risks.
8. What makes SOC operations different from general IT support?
SOC operations focus specifically on security risk, threat detection, and incident handling. Unlike general IT roles that manage system availability or user support, SOC Analysts concentrate on protecting digital assets and maintaining a secure operational environment.
9. What tools does a SOC Analyst use daily?
A SOC Analyst uses a range of tools to monitor, detect, and respond to threats. Common tools include Security Information and Event Management (SIEM) systems that collect and analyze logs and alerts from across systems, Endpoint Detection and Response (EDR) tools to spot suspicious behavior on devices, Extended Detection and Response (XDR) platforms that unify signals from multiple sources, and automation or orchestration tools that help streamline repetitive tasks.
10. What is SIEM in SOC?
SIEM stands for Security Information and Event Management. It is a central tool used in SOCs to gather, correlate, and analyze security event data from systems, networks, and applications in real time. SIEM helps SOC Analysts spot unusual activity by combining logs and alerts into meaningful security events that can be investigated and responded to.
11. What is the difference between SOC L1 and L2?
SOC L1 and L2 differ mainly in responsibility and depth of analysis. An L1 analyst focuses on initial alert review and triage, identifying which issues need further attention. An L2 analyst handles deeper investigation, determines the impact of confirmed threats, and supports incident response and containment.
12. What is the average SOC Analyst salary in India?
In India, the average annual salary for a SOC Analyst is around ₹4.8–5.5 lakh per year, with typical ranges often between ₹3–₹8 lakh depending on experience and city. Some reports show variation across employers and locations, but most SOC Analysts in India fall in this mid-range bracket.





