A cyber security analyst helps protect an organization’s systems, networks, and data from cyber threats. They are the first line of defense, like monitoring activity, spotting vulnerabilities, and responding quickly to any sign of attack.
Their work ensures that the organization’s digital operations remain secure and uninterrupted. From financial systems to employee databases, they keep critical information protected by analyzing threats, reviewing alerts, and applying timely fixes before issues turn into breaches.
The cyber security analyst roles extend more than responding to incidents. They work proactively to strengthen digital defenses through regular firewall upgrades, vulnerability assessments, and secure access management. They also promote cyber awareness within teams, ensuring that safe digital practices become part of the organization’s culture.
Core Roles and Responsibilities of Cyber Security Analyst
A cyber security analyst performs a wide range of responsibilities that safeguard an organization’s digital ecosystem from threats. Their role requires a balance of technical skill, strategic thinking, and constant vigilance because even a single unnoticed vulnerability can expose critical data or disrupt operations.
While the specific duties may vary across industries, the core functions remain consistent worldwide.
Here’s an in-depth look of cyber security analyst job description in their day-to-day work basis:
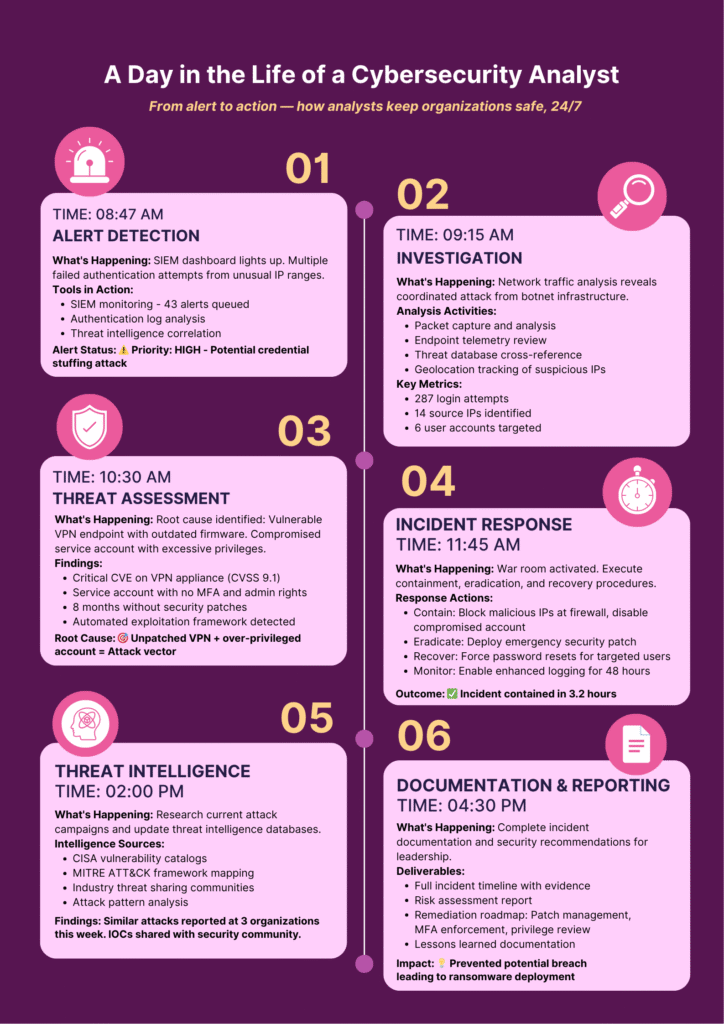
1. Continuous Monitoring of Networks and Systems
A cyber security analyst’s day begins with constant monitoring of the organization’s digital environment. They use tools like SIEM platforms, Intrusion Detection Systems (IDS), and endpoint protection solutions to track logins, data transfers, and network activity.
When something unusual occurs like repeated failed logins or sudden increase in network traffic, the analyst investigates immediately. By catching small irregularities early, they prevent potential breaches and keep systems stable.
However, monitoring alone isn’t enough. To truly secure the network, analysts must also find and fix weaknesses before attackers do; and that’s where next tasks comes in.
2. Vulnerability Assessment and Risk Analysis
Analysts regularly scan security weaknesses across software, networks, and configurations using tools like Nessus, Qualys, or OpenVAS. Once vulnerabilities are identified, they evaluate risk profile and prioritize them accordingly.
For example, a system connected to the internet without recent security updates would be considered high risk because attackers could target it easily.
But identifying risks is only half the job. Analysts also maintain the organization’s defenses by keeping firewalls, antivirus programs, and security patches up to date.
This ongoing maintenance ensures that even after vulnerabilities are fixed, every digital layer remains secure and resistant to new threats.
3. Incident Detection and Response
Even after all known weaknesses are fixed and systems are updated, new threats can still appear at any time. That’s why cyber security analysts stay alert constantly watching for unusual activity or signs of an attack.
When a genuine threat is detected such as unusual file modifications, unauthorized data transfers, or malware activity; analysts act quickly to contain and eliminate it. They may isolate affected devices, block malicious network connections, and remove compromised files to stop the issue from spreading.
After neutralizing the threat, analysts focus on restoring systems to full functionality and verifying that no traces of the attack remain. They also collaborate with IT and management teams to strengthen the affected systems, ensuring similar incidents don’t happen again.
This ongoing cycle of detecting, responding, and improving keeps the organization resilient and ready to face future challenges.
4. Threat Intelligence and Research
Cyber threats evolve daily, with new malware, phishing methods, and hacking tools appearing faster than ever. To stay ahead, analysts continuously gather and study threat intelligence information about current and emerging cyber risks.
They monitor global threat databases, security reports, and dark web sources to spot new attack patterns or vulnerabilities being exploited worldwide.
If a new cyber threat is discovered elsewhere, for example, a ransomware strain targeting a specific software; analysts quickly check whether their organization uses that software and secure it before attackers can strike.
By turning global threat information into local action, cyber security analysts move from simply reacting to predicting; keeping their organizations a step ahead of the ever-changing threat landscape.
5. Security Awareness and Employee Training
Even the most advanced cyber security systems can’t protect an organization if its people are unaware of basic safety practices. That’s why analysts focus on building a security-aware culture across the workplace.
They conduct interactive training sessions to teach employees how to identify phishing emails, use strong passwords, and safely handle sensitive information. Regular awareness campaigns and simulated exercises like phishing tests or mock incident drills help employees practice recognizing and reporting threats in a safe environment.
For example, an employee who learns to spot a fake login page or verify a suspicious email can stop a potential breach before it begins. Through consistent education and real-world simulations, analysts turn employees from potential weak points into active defenders of the organization.
6.Reporting, Documentation, and Compliance
Every action a cyber security analyst takes from detecting threats to responding to incidents must be carefully documented. Detailed records help track what happened, how it was handled, and what improvements were made. These reports are shared with management to review performance and plan security upgrades.
Beyond internal tracking, analysts also ensure that the organization complies with industry and legal standards such as:
- ISO/IEC 27001 – International framework for managing information security.
- GDPR – Governs personal data protection in the European Union(EU).
- HIPAA – Protects patient information in healthcare.
- NIST guidelines – U.S. framework for strengthening cybersecurity practices.
Maintaining proper documentation and compliance records proves that the organization follows best practices and meets all required regulations. It also reduces legal and financial risks by showing clear evidence of accountability in case of audits or investigations.
In short, reporting and compliance turn cybersecurity into an organized, measurable, and legally sound process ensuring that every defense effort is both effective and verifiable.
Start Thinking Like a Cybersecurity Professional
Becoming a cyber security analyst isn’t just about monitoring dashboards or responding to alerts; it’s about thinking ahead of attackers and building systems that stay one step ahead. Every log analyzed, every vulnerability patched, and every employee trained contributes to one goal: keeping the digital world safe.
From scanning networks to managing incidents, analysts are the silent protectors behind every secure system. Their decisions prevent data breaches, protect customer trust, and ensure that organizations can run smoothly even in the face of constant cyber threats.
In a world where digital attacks grow smarter every day, the demand for skilled cyber security analyst job roles is rising fast. If you’re ready to step into this field, focus on mastering not just the tools, but the mindset of an analyst; one that predicts, prevents, and protects.
Explore our Cyber security Course, build to help you develop real-world defensive skills and prepare for one of the most in-demand careers in the digital age.





