Burp Suite vs Postman is a comparison that confuses many beginners because both tools interact with web requests and APIs, yet they are built for very different purposes. Before understanding the tools themselves, it’s important to understand what an API actually is and why APIs matter in modern applications.
An API is simply a way for two systems to communicate. Every website, mobile app, or online service uses APIs in the background to send data between clients and servers. When these communication points fail, applications either stop working correctly or become vulnerable to attacks.
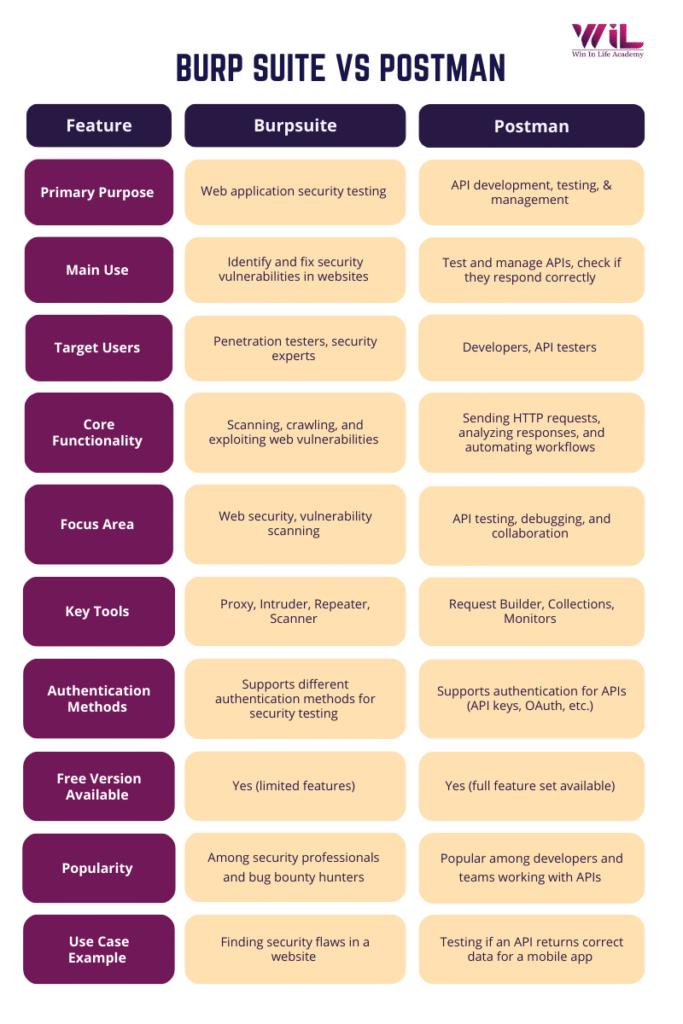
That’s where tools like Burp Suite and Postman come in. One is used to test whether APIs and web applications work as intended. The other is used to test how those same systems behave when someone tries to abuse or break them. Beginners often mix the two because they look similar on the surface, but their roles in real-world workflows are very different.
This guide breaks down Burp Suite vs Postman step by step. You’ll learn what each tool is designed for, how they are used in practice, and which one you should focus on first based on your goals.
|
Featured Snippet Summary Burp Suite vs Postman compares two tools used at different stages of web and API testing. Burp Suite is used for web application and API security testing by intercepting and modifying traffic to find vulnerabilities. Postman is used for API development and functional testing to send requests, verify responses, and validate workflows. Together, they help ensure applications are both secure and reliable. |
What Is Burp Suite?
Burp Suite is a web application security testing tool used to find weaknesses in websites and APIs. It works by sitting between the user and the application and allowing testers to see, intercept, and modify the requests and responses being exchanged.
Instead of checking whether an application works correctly, Burp Suite checks how it behaves when something goes wrong or is intentionally manipulated. This includes changing input values, replaying requests, or sending unexpected data to see if the application breaks or exposes sensitive information.
Burp Suite is widely used as a burp tool for penetration testing because it mirrors how attackers interact with web applications in the real world. Tools like Proxy, Repeater, and Intruder allow testers to manually inspect traffic, resend modified requests, and automate large sets of payloads. This helps uncover issues such as injection flaws, broken authentication, insecure APIs, and improper access control.
For beginners in cybersecurity, Burp Suite is important because it teaches how web vulnerabilities actually appear in live traffic. It moves security testing away from theory and into practical, observable behavior. Check out step-by-step Burp Suite implementation to know how to start practicing Burp Suite.
What Is Postman?
Postman is an API development and functional testing tool used to send requests to APIs and verify that they respond correctly. It allows users to create requests, inspect responses, manage parameters, and organize tests in a structured and repeatable way.
Postman focuses on normal and expected behavior. It is used to confirm that APIs return the correct data, handle inputs properly, and follow the intended workflow defined by developers. This makes it a core tool for API testing and validation during development and quality assurance.
For beginners, Postman simplifies how APIs are understood. Instead of writing code, users can visually build requests, view responses, and test different scenarios. Features like collections, environment variables, and basic test scripts make it easy to scale from simple manual checks to automated API testing workflows.
Postman is not a penetration testing tool. Its role is not to attack or exploit APIs, but to ensure they function reliably before and after deployment. That clear boundary is what separates it from security tools like Burp Suite.
Burp Suite vs Postman – Offensive Security Testing vs Functional API Testing: Differences at a glance
| Category | Burp Suite | Postman |
|---|---|---|
| Core Purpose | Web penetration testing and security testing by intercepting and manipulating web traffic. | API development and functional testing using clean request–response workflows. |
| Target Users | Pentesters, security analysts, bug bounty hunters. | Developers, QA testers, backend/API teams. |
| Key Functional Capabilities | Proxy, Scanner, Repeater, Intruder for security testing. | Collections, environments, test scripts, and mock servers. |
| Real-World Use Cases | Intercepting traffic, fuzzing inputs, exploiting vulnerabilities. | Testing API endpoints, validating workflows, and automating functional tests. |
| Security Testing Strengths | Strong in scanning, fuzzing, and exploiting simulation. | Limited to basic auth, tokens, and HTTPS checks. |
| API Testing Capabilities | Good for API security inspection, not functional testing. | Excellent functional API testing with automation support. |
| Ease of Use | Moderate; requires HTTP and security knowledge. | Easy for beginners; simple GUI and workflow. |
Cybersecurity Fundamentals
Master practical, real-world cybersecurity and ethical hacking skills. This course teaches you how to analyze vulnerabilities, simulate attacks, secure systems, and interpret complex security data. It prepares you for technical roles across SOC operations, penetration testing, and modern security engineering.

Duration: 5 months
Skills you’ll build:
Other Courses
Differences Between Burp Suite and Postman Explained in Detail
Differences by Purpose and Function
Burp Suite
Burp Suite is designed for web application security testing. Its goal is to help security professionals intercept, analyze, and manipulate HTTP/S traffic to uncover weaknesses such as XSS, SQL injection, broken authentication, and insecure session handling. It focuses on understanding how a web application behaves under abnormal or malicious inputs. Burp Suite gives the tester full control over live traffic, making it a core tool for identifying and validating web vulnerabilities.
Postman
Postman is built for API development and functional testing. It enables developers and QA teams to create API requests, test different inputs, verify outputs, and automate workflows. Postman focuses on ensuring APIs work correctly under normal usage. It’s widely used to validate endpoints, test integrations between services, and maintain API reliability across updates.
Differences by How They Are Used in Testing:
Burp Suite
Burp Suite is used during web applications and API security assessments. Testers rely on its interception proxy, Repeater, Intruder, and Scanner to study how an application responds when requests are modified or stressed. It is commonly used in penetration testing, bug bounty hunting, and red team assessments where the goal is to uncover weaknesses attackers might exploit. In practice, API testing using Burp Suite focuses on security validation, such as testing authentication, authorization, and input handling in API endpoints, not functional correctness.
Postman
Postman is used during API development and QA testing. It helps teams test individual endpoints, verify request-response structures, simulate API workflows, and automate repetitive test cases. Its role is functional, not offensive — it ensures that APIs behave as intended and meet the requirements laid out by developers and product teams.
Differences by Automation and Customization Capabilities:
Burp Suite
Burp Suite offers automation focused on web vulnerability scanning and attack simulation. Tools like Scanner automate common vulnerability checks, while Intruder automates custom payload attacks. However, deeper testing often requires manual interaction. Extensions from the BApp Store add more scanning techniques and testing utilities, but the automation aligns mostly with security workflows.
Postman
Postman provides strong automation for functional API testing. Users can write JavaScript-based test scripts, create data-driven testing flows, and run tests automatically using Newman (Postman’s CLI). Postman integrates easily into CI/CD pipelines, enabling automated regression tests every time code is deployed. This makes it a reliable tool for teams managing large or frequently changing APIs.
Differences by Ease of Use:
Burp Suite
Burp Suite has a moderate learning curve, especially for beginners in cybersecurity. To use Burp effectively, you must understand how HTTP requests work, how cookies and sessions behave, and what typical vulnerabilities look like. It is beginner-accessible, but only if the learner has basic web fundamentals. The tool’s depth becomes clearer as the learner grows in security knowledge.
Postman
Postman is significantly easier for beginners. You can start using it immediately without understanding security concepts. Even someone new to APIs can quickly send requests, inspect responses, and build simple workflows. Its visual layout and guided experience make it an ideal entry point for learning how APIs work in general.
Differences by Reporting and Documentation Capabilities:
Burp Suite
Burp Suite generates detailed vulnerability reports that include severity levels, technical descriptions, and remediation guidance. These reports are used in client deliverables, audits, and compliance documentation. Its reporting system is tailored for web security assessments and is structured around vulnerabilities discovered during testing.
Postman
Postman excels at API documentation, not vulnerability reporting. It automatically generates user-friendly API documentation from the requests and collections created by developers. These documents help teams understand how endpoints work and act as onboarding material for new developers. Postman’s documentation is built around clarity and usability rather than security findings.
Differences by Extensibility and Ecosystem:
Burp Suite
Burp Suite supports extensions through the BApp Store and the Burp Extender API. These additions enhance scanning, payload generation, traffic visualization, and custom testing workflows. The ecosystem is centered around web and API security, giving users advanced tools to deepen their penetration testing capabilities without changing Burp’s core purpose.
Postman
Postman integrates with a wide range of development and DevOps tools — API gateways, CI/CD pipelines, cloud platforms, and monitoring systems. It also supports public API collections that teams can import and test instantly. The ecosystem is built around API lifecycle management, enabling better collaboration, testing, automation, and documentation across development teams.
Burp Suite or Postman – Which One Should You Learn First?
Choosing between Burp Suite and Postman depends entirely on the direction you want to take as a beginner. Both tools are important, but they solve different problems, so your choice should match your career path.
Learn Burp Suite First if You Want to Focus on Web Security
If you’re aiming for cybersecurity or penetration testing, start with Burp Suite. It teaches you how real web traffic works, how vulnerabilities show up in requests, and how attackers exploit weak points in applications. Since most modern security issues originate from poorly protected web apps and APIs, Burp gives you hands-on exposure to what actual attacks look like. It’s the right first step if you want to move into ethical hacking, application security, or bug bounty testing.
Learn Postman First if You Want to Focus on API Development and Testing
If your interest leans toward development, QA, or backend engineering, start with Postman. It helps you understand how APIs function, how data moves between systems, and how to test endpoints in a structured way. You’ll learn how to build requests, validate responses, and automate basic tests; all essential skills in modern microservice-based environments. Postman is the better starting point if you want to work in software testing, backend/API development, or DevOps pipelines.
Certified Ethical Hacker – CEH v13 AI
Gain job-ready ethical hacking skills through a fully hands-on, AI-powered CEH training path. Learn how modern attacks actually work, practice them in real labs, and build the technical depth needed for penetration testing and cybersecurity roles.

Duration: 6 months
Skills you’ll build:
Other Courses
Case Study 1: How Burp Suite Found a Critical Security Flaw in a Magento E-Commerce Site
Background
Magento is a popular platform used to build online shopping websites. These sites store sensitive information like customer details and order data, which makes them attractive targets for hackers.
PortSwigger, the company behind Burp Suite, tested Magento’s LUMA demo store to show how real attackers could find weaknesses in an e-commerce website before criminals do.
The Problem
One of the most dangerous threats to websites is SQL injection. This happens when a website incorrectly handles user input and accidentally allows attackers to run database commands. If successful, attackers can read, change, or steal all stored data.
The goal was to check whether the Magento store could be tricked into running harmful database commands.
How Burp Suite Was Used (Step by Step)
Burp Suite was used as an attacker would use it, but in a safe and controlled way.
- Step 1: Discovering the website’s pages
Burp Suite automatically browsed the website to find all pages, forms, and input fields. This helps testers understand where users can enter data.
- Step 2: Automatically checking for weak spots
Burp Suite then sent common attack patterns into those input fields to see if the website behaved strangely. This step quickly highlighted areas that looked vulnerable.
- Step 3: Manually testing suspicious inputs
Testers took one of the suspicious requests and slightly changed the data being sent. By sending the same request again and again with small changes, they confirmed that the website was treating user input as database commands.
- Step 4: Automating repeated attack attempts
Once the weakness was confirmed, Burp Suite was used to repeatedly test different input combinations. This showed that database information could be extracted step by step.
Results
The test proved that:
- The website had serious security flaws
- Attackers could access the backend database
- Sensitive system information could be exposed
Outcome
These findings were reported to Magento’s security team, who fixed the issue before attackers could exploit it publicly.
This case shows how Burp Suite, as a burp tool for penetration testing, helps organizations find and fix dangerous security flaws early, before real damage happens.
Case Study 2: How Postman Helped a Fintech Company Fix API Testing and Onboarding Problems
Background
Canopy Servicing is a fintech company that provides APIs for loan servicing. Other companies rely on these APIs to build financial products, so accuracy and reliability are critical.
From the start, Canopy’s platform depended heavily on APIs to handle users, payments, and accounts.
The Problem
As the company grew, they faced multiple issues:
- Developers struggled to understand how the APIs worked
- New clients took weeks to integrate
- Manual testing missed errors, causing problems in production
- Teams worked in silos with no shared testing process
These issues slowed growth and increased support costs.
How Postman Was Used (Step by Step)
Postman was introduced to bring structure and clarity.
- Step 1: Creating a single place for API details
All APIs were documented inside Postman so developers and clients could clearly see how each API works and what data it expects.
- Step 2: Testing APIs the way users actually use them
Instead of testing one request at a time, teams tested complete user journeys like onboarding a borrower or processing a payment.
- Step 3: Repeating tests automatically
Postman was set up to automatically run tests whenever changes were made. This reduced human error and caught problems early.
- Step 4: Team collaboration and sharing
Teams and clients could reuse the same API tests, saving time and preventing duplicate work.
Results
The changes led to:
- Faster client onboarding, reduced from weeks to days
- Fewer bugs reaching production
- Faster API development cycles
- Better communication between teams and customers
Outcome
Postman helped Canopy move from scattered, manual API testing to a clear, repeatable, and reliable API testing process. This made their platform easier to use, easier to scale, and easier to maintain.
Conclusion
Burp Suite vs Postman is not about choosing a “better” tool. It’s about understanding what you are testing and why. Burp Suite exists to expose how web applications and APIs fail under hostile or malicious conditions. Postman exists to confirm that APIs behave correctly under normal, expected use. Confusing these roles is the fastest way for beginners to learn the wrong skills.
Modern applications don’t break at the UI level. They break at communication points APIs, authentication flows, input validation, and session handling. Burp Suite shows you how those points collapse when abused. Postman shows you how they behave when everything is supposed to work. That distinction is the line between functional testing and security testing, and it’s non-negotiable in real-world environments.
This is exactly why both tools are taught inside structured cybersecurity learning paths. At Win In Life Academy, learners don’t just “learn tools.” They learn when to use Burp Suite, when to use Postman, and why those decisions matter in real security workflows. The focus stays on understanding application behavior first, then learning how attackers exploit weaknesses, and finally learning how to defend against them.
The industry doesn’t reward people who collect tools. It rewards people who understand systems deeply and can identify where and how they fail. If you’re serious about building skills that hold up in real security roles, learning Burp Suite and Postman in the right context is not optional. It’s the baseline.
Frequently Asked Questions (FAQs) – Burp Suite vs Postman
1. Can I use Burp Suite and Postman together for API testing?
Yes. This is a common real-world setup. Postman is used to create and send API requests easily. That traffic can then be passed through Burp Suite to inspect and test it for security issues. Postman handles functional testing, while Burp Suite handles security testing. Together, they give a complete view of how an API works and how it can fail.
2. Which tool should I learn first: Burp Suite or Postman?
It depends on your goal. Learn Postman first if you want to work in API development, QA, or backend roles. Learn Burp Suite first if you want to move into cybersecurity or penetration testing. Starting with the wrong tool often wastes time, so align your choice with your career path.
3. Is Burp Suite suitable for beginners?
Yes, but with conditions. Burp Suite has a free Community Edition that beginners can use. However, it assumes you understand basic web concepts like HTTP requests, cookies, and sessions. It is not beginner-friendly in the same way Postman is, but it becomes manageable once you understand web fundamentals.
4. What is the cost difference between Burp Suite and Postman?
Postman offers a very generous free plan that is enough for most beginners and small teams. Burp Suite also has a free version, but advanced features like automated vulnerability scanning are paid. Burp Suite Professional is significantly more expensive, which reflects its focus on security testing rather than general API testing.
5. Can Burp Suite test APIs for functional correctness like Postman?
No. Burp Suite is not designed to check whether an API works correctly. It does not validate business logic or expected responses. Its purpose is to test security by manipulating requests and finding vulnerabilities. For functional API testing, Postman is the right tool.
6. What vulnerabilities can Burp Suite detect that Postman cannot?
Burp Suite can detect security flaws such as SQL injection, cross-site scripting, broken authentication, insecure access control, and other weaknesses caused by improper input handling. Postman is not built to discover or exploit vulnerabilities; it focuses on normal API behavior.
7. Do I need penetration testing experience to use Burp Suite?
No, but you do need basic web knowledge. Understanding HTTP requests, cookies, sessions, and authentication concepts is enough to get started. Many beginners learn Burp Suite by practicing on intentionally vulnerable applications designed for training.
8. Can Postman automate security testing?
Postman can automate basic checks like authentication handling, response validation, and status codes. However, it cannot perform real security testing such as vulnerability scanning, fuzzing, or exploitation. Postman automation is for functional reliability, not security assurance.
9. Is it legal to use Burp Suite for penetration testing?
Yes, but only with permission. You can legally use Burp Suite on applications you own or have written authorization to test. Using it on systems without permission is illegal. The tool itself is legal; misuse is not.
10. What’s the difference between Burp Suite Community, Professional, and Enterprise editions?
Community Edition is free and meant for learning and manual testing.
Professional Edition adds automated vulnerability scanning, faster testing, and reporting, and is used by working security professionals.
Enterprise Edition is designed for large organizations that need centralized scanning, reporting, and compliance support.
Beginners can start with Community Edition. Professionals typically move to Professional once they work on real projects.





