If you’re confused about whether to learn Burp Suite or Metasploit, you’re not alone. This Burp Suite vs Metasploit dilemma is one every beginner faces. Both tools look powerful, both are widely used by ethical hackers, and both appear in cybersecurity job descriptions. However, they serve completely different purposes, and choosing the right one early can save you a lot of time and effort
This guide gives you a clear, practical breakdown of what each tool actually does, where they fit in real penetration testing, and which one you should start with based on your career path. Simple, direct, and built around what beginners actually search for.
What is Burp Suite?
Burp Suite is an integrated platform used for web application security testing. It helps cybersecurity professionals identify, analyze, and fix vulnerabilities in web applications, focusing on vulnerabilities such as SQL injection and cross-site scripting (XSS). Widely used in penetration testing and ethical hacking, Burp Suite simulates real-world attacks to find and assess weaknesses before they are exploited by attackers. It is a core tool for web security assessments and is often employed in bug bounty programs and security audits.
What is Metasploit?
Metasploit is an open-source penetration testing framework that allows cybersecurity professionals to identify, exploit, and validate vulnerabilities in systems and networks. It is widely recognized for its ability to simulate real-world attacks and test the effectiveness of security defenses. Metasploit is used in system and network exploitation, enabling testers to automate attacks and create custom exploits. It plays a critical role in offensive security, red teaming, and vulnerability assessments, focusing on system-wide security testing rather than web app vulnerabilities.
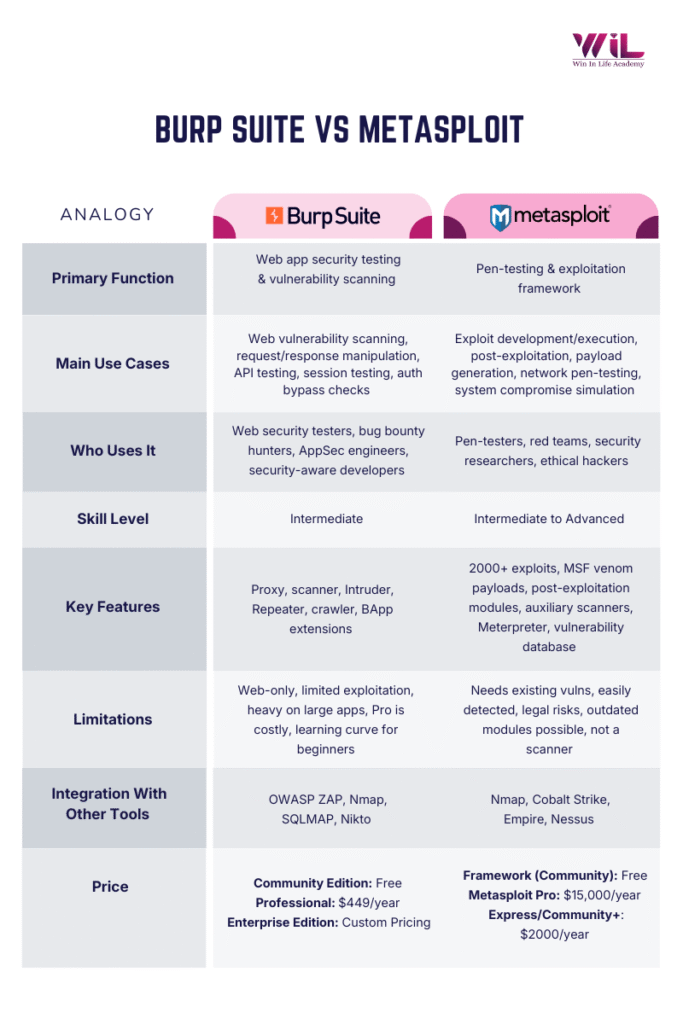
Burp Suite Vs Metasploit – Differences at a Glance
| Feature | Burp Suite | Metasploit |
|---|---|---|
| Primary Focus | Web Application Security | System and Network Exploitation |
| Type of Testing | Web app vulnerabilities (e.g., XSS, SQLi) | System vulnerabilities (e.g., RCE, SMB) |
| Core Functionality | Intercept and analyze web traffic, scan for vulnerabilities, and simulate attacks on web apps | Exploit vulnerabilities in systems, simulate attacks, post-exploitation activities |
| Limitations | Limited to web apps, less effective for network/system exploitation | Doesn’t specialize in web app vulnerabilities, focused more on system/network exploitation |
| Ease of Use | User-friendly for web security professionals | Requires advanced knowledge for system exploitation and creating custom exploits |
Core Differences Between Burp Suite and Metasploit Tool
Differences by Purpose and Function
Burp Suite:
Burp Suite is tailored for web application security, designed to intercept web traffic, scan for vulnerabilities, and simulate attacks within the web application layer. It helps penetration testers identify and fix vulnerabilities like XSS, SQL injection, and session management flaws in web apps and APIs, providing a comprehensive assessment of web-specific threats.
Metasploit:
Metasploit, on the other hand, focuses on system and network exploitation. It is a comprehensive framework for identifying and exploiting vulnerabilities in network services and operating systems, automating attacks, and performing post-exploitation activities. Metasploit allows penetration testers to simulate real-world cyberattacks, assess the resilience of system defenses, and exploit system-level flaws like RCE, SMB vulnerabilities, and privilege escalation.
| PROFESSIONAL CERTIFICATE IN Cybersecurity Fundamentals Master practical, real-world cybersecurity and ethical hacking skills. This course teaches you how to analyze vulnerabilities, simulate attacks, secure systems, and interpret complex security data. It prepares you for technical roles across SOC operations, penetration testing, and modern security engineering. IN PARTNERSHIP WITH IBM ⭐ 4.8 (3,235 ratings) View Course – (https://wininlifeacademy.com/cyber-security-course/) Duration: 5 months Skills you’ll build: |
Cybersecurity Fundamentals
Master practical, real-world cybersecurity and ethical hacking skills. This course teaches you how to analyze vulnerabilities, simulate attacks, secure systems, and interpret complex security data. It prepares you for technical roles across SOC operations, penetration testing, and modern security engineering.

Duration: 5 months
Skills you’ll build:
Network Security
Web Application Security
Malware Analysis
OSINT & Information Gathering
Phishing & Social Engineering
Linux for Security
Penetration Testing Tools (Nmap, Metasploit, Burp)
Defensive Security & IDS/IPS
Other Courses
| Ethical Hacking Network Security Web Application Security Malware Analysis OSINT & Information Gathering Phishing & Social Engineering Linux for Security Penetration Testing Tools (Nmap, Metasploit, Burp) Defensive Security & IDS/IPS |
| Other Courses |
Differences by How the Tools are Used in Penetration Testing
Burp Suite:
Burp Suite is primarily used during the early stages of penetration testing, particularly when assessing web applications for vulnerabilities. It’s widely used in bug bounty programs and security audits where the goal is to test the security of web apps and their APIs.
Metasploit:
Metasploit is employed when deeper system-level exploitation is required. It’s ideal for network penetration testing, red team operations, and simulating real-world cyberattacks across systems and networks. It is used after vulnerabilities have been identified and focuses on exploiting and testing system security.
Differences by How the Tool Can be Automated and Customized
Burp Suite:
Burp Suite’s automation capabilities are focused on common web vulnerabilities like XSS and SQL injection. It can automatically scan these vulnerabilities across web applications, but its customization options are more manual. Tools like Repeater and Intruder allow testers to perform customized attacks on specific web elements, though the level of automation is more suited for standard web security assessments.
Metasploit:
In contrast, Metasploit provides extensive automation for system and network exploitation. It allows penetration testers to automate complex attack chains, using pre-built exploit modules and payloads. Metasploit also offers the ability to create custom exploits and tailor payloads to specific system vulnerabilities, making it highly customizable for advanced exploitation scenarios. It is designed for more advanced users who need precision and flexibility when targeting vulnerabilities in network infrastructure or operating systems.
Differences by Beginner-friendliness
Burp Suite:
Burp Suite is user-friendly and designed for professionals who specialize in web application security. It is accessible to both beginners and intermediate testers, making it ideal for web security professionals who focus on testing and securing web apps and APIs.
Metasploit:
Metasploit, however, requires advanced knowledge of system exploitation and network penetration. It has a steeper learning curve, requiring a deeper understanding of network protocols, exploit development, and post-exploitation techniques, making it more suitable for advanced penetration testers.
Differences by Reporting and Documentation Capability
Burp Suite:
Burp Suite provides detailed reports on web vulnerabilities, making it useful for compliance audits and client-facing reports. Its reporting system is structured and tailored for web application security assessments.
Metasploit:
Metasploit’s reporting features are more basic, focused on the results of exploitation rather than generating client-ready reports. Its primary strength lies in exploit execution and post-exploitation analysis, not in reporting or documenting vulnerabilities.
Differences on Adding Extensions and Customization
Burp Suite:
Burp Suite allows users to enhance its functionality by adding extensions from the Burp Suite App Store. These extensions are primarily designed to improve web application testing capabilities, such as adding new scanning techniques or custom scripts. The App Store provides a wide range of tools that allow users to expand Burp Suite’s capabilities without altering its core framework, making it ideal for customizing web testing.
Metasploit:
Metasploit, on the other hand, supports extensive customization through the creation of custom modules, including exploits, payloads, and reconnaissance tools. Unlike Burp Suite, Metasploit is geared towards system exploitation and network testing, and it integrates seamlessly with other tools like Nmap and Wireshark to expand its network assessment capabilities. The flexibility in creating custom modules makes Metasploit suitable for advanced exploitation tasks across diverse security assessments.
Burp Suite or Metasploit – Which One Should I Learn First
Deciding whether to start with Burp Suite or Metasploit depends on where you want to focus your efforts on cybersecurity. Both tools are essential for penetration testing. If you are a beginner and want to have a career in cybersecurity, this is what you can do.
Start with Burp Suite First if You Want to Focus on Web Security
If you are new to cybersecurity and penetration testing, starting with Burp Suite helps you build the fundamentals of web application security. Since web vulnerabilities are one of the most common security threats today, learning to test web applications and APIs first gives you a clear path into many entry-level cybersecurity roles.
Start with Metasploit First if You Want to Explore System and Network Exploitation
If you’re aiming for a more advanced and broad approach to cybersecurity, then Metasploit could be the better starting point. By learning Metasploit first, you’ll develop a broader understanding of penetration testing, moving from web vulnerabilities to network-level exploitation. Starting with Metasploit helps you learn offensive security techniques at a system-wide level and prepares you for more complex attack simulations.
| PROFESSIONAL CERTIFICATE IN Certified Ethical Hacker – CEH v13 AI Gain job-ready ethical hacking skills through a fully hands-on, AI-powered CEH training path. Learn how modern attacks actually work, practice them in real labs, and build the technical depth needed for penetration testing and cybersecurity roles. IN PARTNERSHIP WITH IBM ⭐ 4.8 (3,235 ratings) View Course – (https://wininlifeacademy.com/certified-ethical-hacker/) Duration: 6 months Skills you’ll build: |
| Ethical Hacking & Recon Web & Network Exploitation Malware, Ransomware & OSINT Wireless Attacks & MITM Cryptography & Steganography Automated Scanning & VAPT Tools Post-Exploitation & Defense Techniques |
| Other Courses |
1. Case Study: Web-Application Penetration Testing and Exploitation with Burp Suite
A 2024 research study titled “Advanced Vulnerability Detection and Exploitation in Web Applications Using Burp Suite” evaluated real web applications using Burp Suite’s full suite of scanning and exploitation tools.
The study found multiple high-severity vulnerabilities across test applications, including SQL injection, XSS, insecure session handling, and insecure authentication flows, proving that web apps continue to be a major attack surface in 2024–2025. This research highlights how even modern applications remain vulnerable to web-layer attacks and confirms the need for continuous and methodical security testing.
Process: How Burp Suite Was Used in the Study
The research used a structured penetration-testing methodology powered by Burp Suite, focusing on:
- Scanner — to automatically detect common vulnerabilities such as XSS, SQLi, and HTML injection.
- Intruder — perform brute-force and parameter-tampering attacks.
- Repeater — to manually manipulate HTTP requests and validate vulnerabilities.
- Spider — to map the full application structure and uncover hidden attack surfaces.
- Collaborator — tests out-of-band vulnerabilities.
The study systematically demonstrated Burp Suite’s capability to uncover vulnerabilities that traditional automated scanners and static code analysis tools failed to detect.
Results: Proven Effectiveness of Burp Suite in Real Testing Environments
The study reported that Burp Suite:
- Identified dozens of critical vulnerabilities across multiple applications.
- Detected XSS variants and SQL injection flaws that were not identified by other scanners.
- Revealed session management weaknesses, such as insecure cookies and missing security flags.
- Validated that certain vulnerabilities were exploitable through manual Repeater-based exploitation.
- Demonstrated the importance of combining both automated scanning and human-driven testing, which Burp Suite supports perfectly.
The outcome of this research reinforces that Burp Suite is one of the most reliable tools for real-world web-application security testing, enabling security professionals to detect and confirm vulnerabilities before attackers can exploit them.
2. Case Study: System-Level Exploitation Using Metasploit.
A 2025 study titled “Secure Framework for Developing and Executing Exploits Against Vulnerable Systems” demonstrated how Metasploit is used to exploit system-level vulnerabilities in a controlled security-testing environment. The research focused on validating real-world risks in vulnerable operating systems and assessing how attackers could gain full system access through known exploits.
Process: How Metasploit Was Used in the Study
The research followed a structured exploitation workflow using the Metasploit Framework, involving:
- Reconnaissance & Scanning: Identifying open ports and vulnerable services in the target environment.
- Exploit Selection: Choosing appropriate exploits from Metasploit’s exploit modules tailored to the target OS.
- Payload Deployment: Delivering custom payloads to gain remote access and bypass system defenses.
- Post-Exploitation: Using Meterpreter for deeper access — privilege escalation, data extraction, and system control.
The study demonstrated that Metasploit’s modular architecture allows testers to develop, configure, and execute exploits with high precision during penetration testing scenarios.
Results: Proven Effectiveness of Metasploit in Real Exploitation
The research confirmed that Metasploit was able to:
- Successfully exploit critical vulnerabilities in the test system.
- Achieve remote system access through deployed payloads.
- Perform post-exploitation actions, including privilege escalation.
- Validate how easily unpatched system vulnerabilities can lead to full system compromise.
The findings reinforce why Metasploit remains a leading framework for system and network exploitation, providing penetration testers with the capabilities needed for advanced attack simulations, red-team activities, and validating real-world system risks.
Conclusion
As we’ve explored this blog, mastering tools like Burp Suite and Metasploit are critical for identifying and addressing vulnerabilities in web applications, systems, and networks. Whether you’re focused on securing web applications or diving into broader system exploitation, these tools are essential for anyone serious about cybersecurity.
At Win in Life Academy (WILA), we provide industry experts-designed cybersecurity course that includes all these tools and more to develop hands-on skills to stay ahead in this ever-evolving field. If you’re ready to turn your passion for cybersecurity into a career and learn from experts who guide you every step of the way, enroll today and take the first step toward securing your future in cybersecurity!
FAQs
1. What is Metasploit used for?
It’s used to discover vulnerabilities, run exploits, and simulate attacks to test how secure a system really is.
2. What is Burp Suite used for?
It’s used to intercept, modify, scan, and analyze web requests to identify security flaws in websites and web apps.
3. What is the difference between Burp Suite and Metasploit?
Burp Suite helps you find weaknesses in a web app by intercepting and testing requests.
Metasploit helps you exploit those weaknesses to show the real impact of a hack.
4. Is Burp Suite free?
The basic version is free. The Pro version costs money but gives you faster scanning, automation, and advanced tools.
5. Is Burp Suite like Wireshark?
Not really. Wireshark captures and analyzes network packets. Burp Suite focuses only on web traffic and web application testing.
6. Is Metasploit free to use?
Yes. Metasploit Framework is completely free and open-source. Only the commercial Pro version is paid.
7. Do hackers use Metasploit?
Absolutely. Ethical hackers use it for testing, and real attackers use it because it automates many powerful exploits.
8. Is Metasploit a SIEM tool?
No. SIEM tools collect and analyze logs. Metasploit is for offensive testing and exploitation, not monitoring.
9. Is Burp Suite a DAST tool?
Yes. It tests an application from the outside while it’s running, just like an attacker would.
10. Is Burp Suite part of Kali Linux?
Yes. Kali includes Burp Suite Community Edition by default, so you can start using it immediately.





